CIA (Confidentiality, Integrity, Availability)
Course Overview
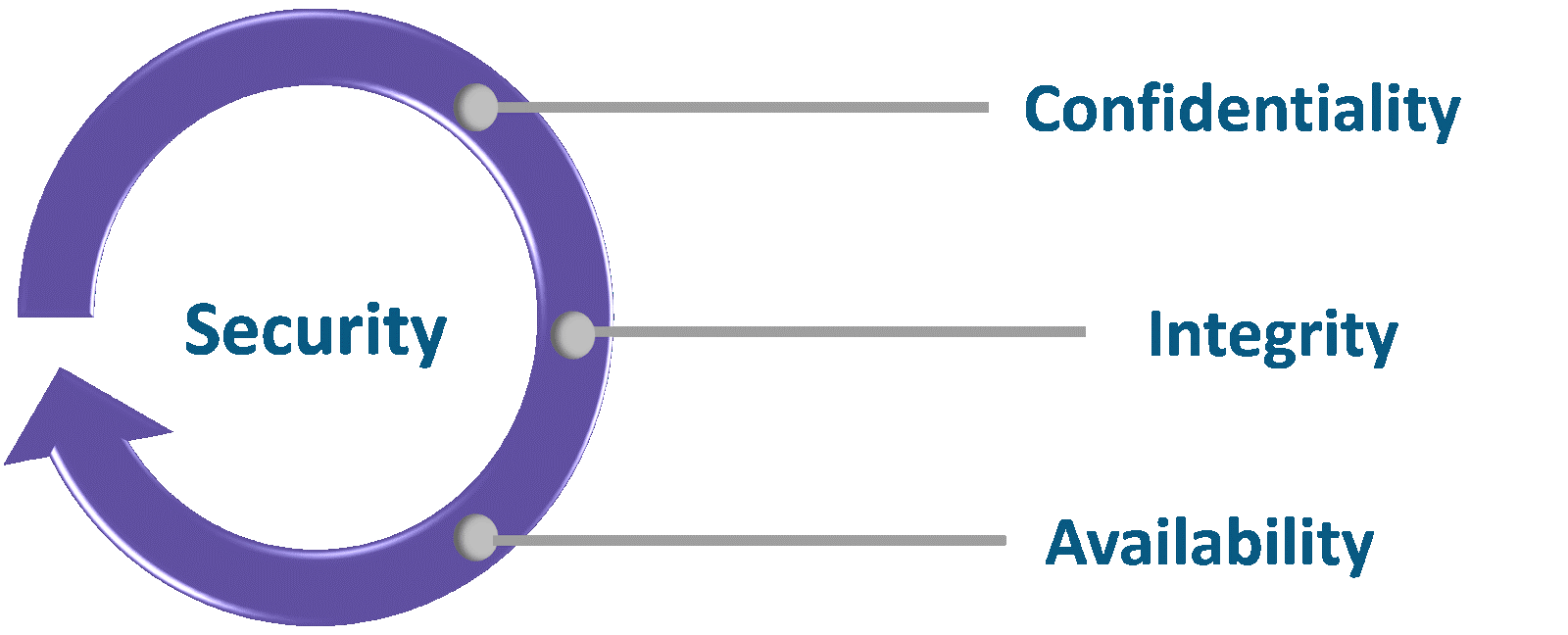
The CIA Triad is the cornerstone of information security, focusing on the three critical principles that guide how organizations safeguard their data and systems. This course explores the concepts of Confidentiality, Integrity, and Availability and their application in ensuring secure information systems. Understanding the CIA Triad is essential for professionals in cybersecurity, network administration, and IT management. By the end of the course, learners will be equipped with the knowledge to apply these principles in various real-world scenarios to protect sensitive data, prevent unauthorized access, and ensure the availability of critical systems.
Pre-requisite
- Basic understanding of information systems, networks, and cybersecurity principles.
- No specific prior experience required, but familiarity with IT and security concepts is helpful.
Benefits
- Fundamental Security Understanding: Learn the essential principles of information security that guide all security measures.
- Data Protection: Gain skills to protect sensitive information from unauthorized access and ensure it remains accurate and reliable.
- Risk Management: Understand how to assess and manage risks to system availability and data integrity.
- Improved Security Framework: Develop the ability to apply the CIA Triad in designing secure systems and networks.
- Career Enhancement: Strengthen your cybersecurity knowledge and skills for roles in IT security, network administration, and more.
Who Should Take This Course?
- Cybersecurity Professionals: Individuals responsible for safeguarding data and systems from cyber threats.
- Network and Systems Administrators: Professionals tasked with ensuring the security and availability of IT infrastructures.
- Data Protection Officers: People managing compliance with privacy laws and regulations regarding data protection.
- IT Managers and Directors: Leaders in organizations looking to understand how to build and maintain secure systems.
- Students and Beginners: Those new to cybersecurity who wish to understand the foundational principles of information security.
